In recent years, there have been notable advancements in patient data security with EHR software across the United States. These developments have focused on safeguarding patient data and ensuring compliance with regulatory standards. However, hacking and breach of digital privacy are very common in recent times. With sensitive lab information and prescription details available in the palm of your hand, how well can private information be safeguarded? Let’s find out.
Heightened Emphasis on Patient Data Security
EMR software vendors are hyperaware of the sensitivity of patient information stored within EMR systems. Hence, to avoid the possibility of data breaches they prioritize data security. They do this in many ways:
- Robust encryption methods
- Stringent access controls
- Regular security audits etc.
Compliance with Cybersecurity Regulations
The Health Insurance Portability and Accountability Act (HIPAA) has established guidelines for safeguarding patient health information. HIPAA compliance is crucial for both EMR software vendors and healthcare providers to operate in the USA. Therefore, EHR software vendors are keen to ensure they have implemented appropriate safeguards to secure patient data within EMR systems.
Adoption of Cybersecurity Best Practices
EMR software vendors are increasingly adopting industry best practices to strengthen cybersecurity measures. This includes:
- Conducting regular security assessments
- Employing vulnerability testing
- Implementing multi-factor authentication
- Utilizing intrusion detection systems
- Following secure coding practices
As a result, these measures minimize vulnerabilities and protect against potential cyber threats.
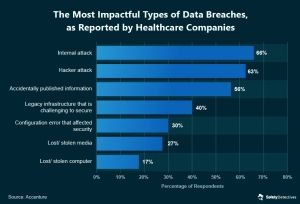
Biggest Threats To Data Security
Implementation of Threat Intelligence and Monitoring
Furthermore, EHR software vendors are incorporating threat intelligence and monitoring systems into their solutions. What this means is that these systems don’t only stop data hacking they track potential threats and stop them from occurring. By analyzing network traffic and identifying potential threats, the EMR software provides real-time alerts to prevent security breaches. Continuous monitoring helps detect and respond to cyber threats promptly.
User Training and Awareness for Patient Data Security
Along with creating airtight security software, EMR software vendors also recognize the significance of user training and awareness. A tool is only as effective and useful as the person who wields it. As a result, healthcare organizations are implementing programs to mitigate cybersecurity risks. Software vendors also provide training to healthcare professionals and staff.
Once they are trained to identify data security threats, healthcare providers and staff will be able to prevent these data breaches successfully.
Cybersecurity Partnerships and Collaborations
And finally, healthcare organizations and EMR software vendors are establishing partnerships and collaborations with cybersecurity firms and organizations. These collaborations result in tighter security all around.
The sharing of threat intelligence, information, and analysis centers (ISACs) also helps with the research and development of healthcare-specific cybersecurity solutions.
It’s important to note that the cybersecurity landscape is dynamic and continually evolving. Therefore, it is vital for healthcare organizations and EMR software users to remain updated on the latest cybersecurity developments.








